How can we trust our elections?
Gov. Romney may end up in the White House not because the majority of voters choose him, but because Pres. Obama’s lead may not be large enough to survive the obstacles his supporters will face on the way to the voting booth, and inside it. The Obama supporters who will not be allowed to vote, or whose votes, once cast, will not be counted, may be in numbers high enough to put the wrong man in the White House. Again. We all know, and most of us acknowledge, that the photo ID laws and the purging of voter rolls disenfranchises many legitimate voters, and these voters are not evenly distributed among voter demographics. That burden falls most heavily onto college students, the elderly poor, and racial minorities. Guess how they usually vote.
I’m taking a coursera course, Securing Digital Democracy, from the University of Michigan. Most of what we’re learning, I already knew in general terms, but this course is revealing the details. Especially interesting to me are the intricate innards of the voting machines which were implicated in putting George W. Bush into the White House.
Code might be a million lines long. Any typos? Any errors? Any malicious code? What happens is unobservable. The process is secret.
The ways that these machines can miscount votes, either because of design flaws that have been discovered and reported but not corrected, or by deliberate manipulation, are too many to list. I take notes as I watch these lectures, with pen on paper, and my spiral notebook contains eight pages of ways these machines can miscount votes. In most cases, the software running the vote has never been tested. No independent tests. Diebold has threatened election officials with loss of their job if they request independent testing.
Instead of a hand behind a curtain, we have a secret program developed by a private company. We can’t see the code, but hey, it was approved by our government, so what could go wrong? Right?
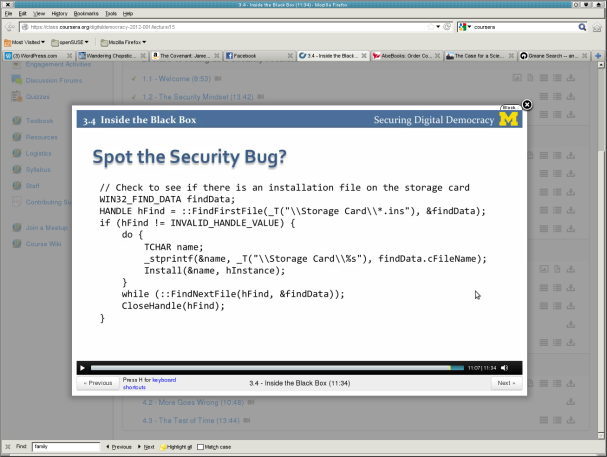
Some of the troublesome source code is revealed and explained in the course. In some cases the teacher points out the errors, and in some he simply says, see if you can find the errors.
Here is an example of the latter. I cannot find the error(s).
Computer Science departments were able to get hold of actual voting machines (through cloak and dagger adventures that I won’t go into here) and find hardware flaws as well. The many ways the votes can be changed involve the removable memory chips, the locks, the bootloader, the encryption keys, the memory cards, and the jumpers on the motherboard, to name just a few.
Memory cards (holding the votes) could easily be replaced without leaving evidence. And the machines were left unlocked in schools and other public buildings so that anyone with access could replace a memory card. A person with even brief access (the computer has a locked compartment, but the lock can be picked in about 10 seconds) can replace memory cards or even replace a chip that will cause the machine to boot to another program other than the vote recording program.
Once in, a hacker can even change the code so that when a vote is cast for Candidate X, the machine records a vote for Candidate Y, but the paper record shows that the voter voted for Candidate X, assuring the voter that all went well. This kind of malicious code is not as likely, as it would be caught in the case of an audit, but only in the case of an audit, and most precincts don’t end up in an audit.
Our voting machines are tested by independent testing authorities. The testing companies are chosen by the voting machine companies and paid by them. After machines are certified by ITAs, independent computer experts have found flaws that allow votes to be changed without detection. Every independent testing has found serious flaws in machines that have been certified.
There is great incentive in a competitive market for ITAs to produce a glowing report, and no requirement that flaws be reported.
Exit polls were extraordinarily reliable predictors of wins until computer counting became the prevalent means of deciding outcomes. There is overwhelming evidence that exit polls are more reliable than the counts reported by private proprietary secret computer codes. Yet the National Election Pool had made a decision to eliminate exit polling in the 2012 election in 19 states. This further erodes election integrity.
All this is troublesome, but it requires citizens to learn about the troubles. And that’s not easy. So should we just trust our elections to private corporations with secret codes? What could go wrong?
See the answer here, at Voting Machines, again.







15 comments